DHCP is a useful protocol for IP auto-configuration. Instead of assigning IP manually to every computers that are connected to IP networks, DHCP provides administrators a flexible, convenient and efficient way.
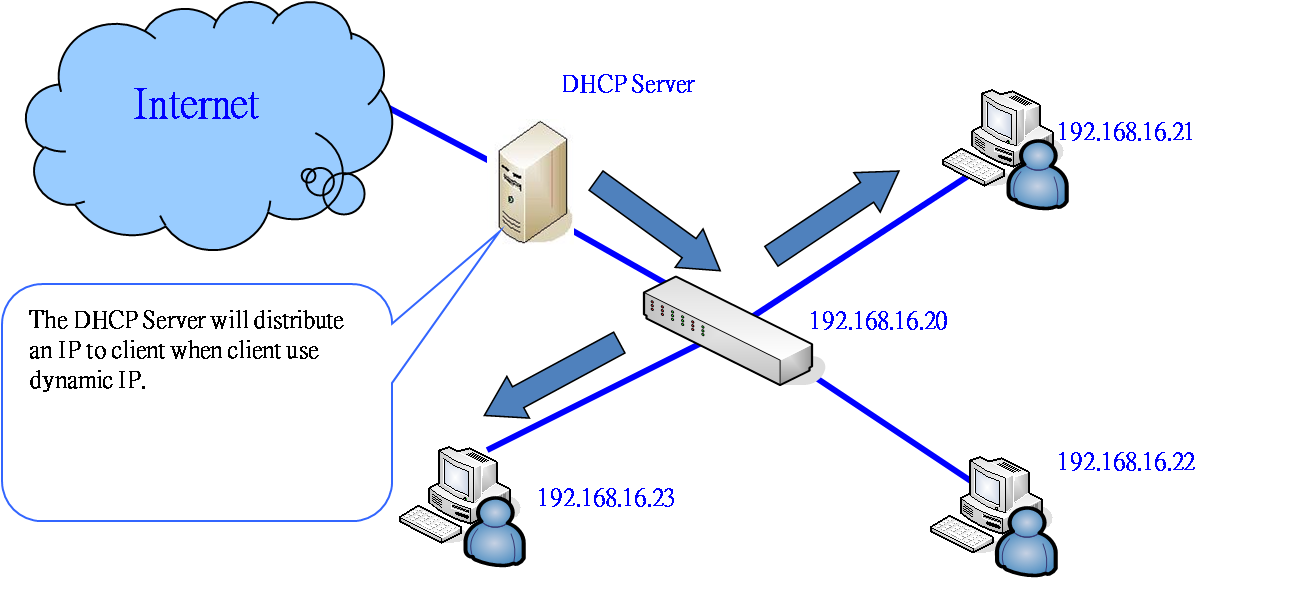
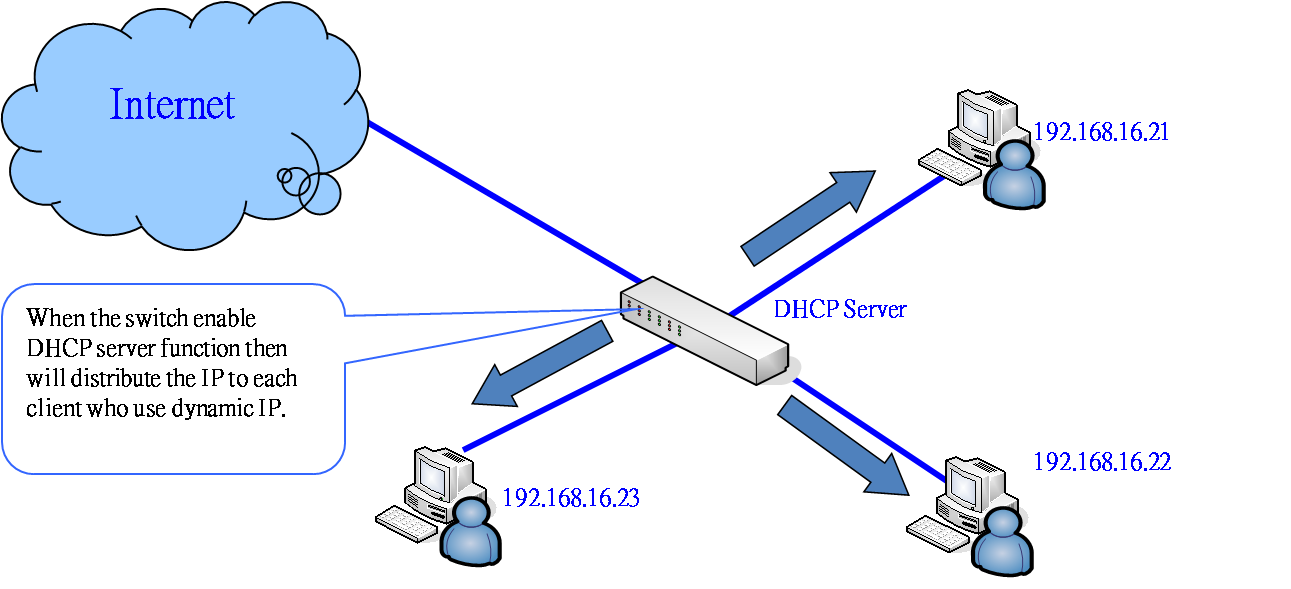
There’re two roles in DHCP protocol: server and client. Switches may support only DHCP client or both DHCP server and client. When DHCP client function is enabled, the switch will be assigned an IP address from the network DHCP server. The default IP address will be replaced by the assigned IP address on DHCP server. When the switch supports DHCP server and the function is active, the system will collect the DHCP client information dynamically. Once a device is connecting to the port and asks for IP assigning, the DHCP server will assign the IP address from the range that set by administrator. The central database that DHCP server provides can prevent two computers from being configured with the same IP accidently.
All of Lantech smart/ managed switches support DHCP client function and most of the managed switches support server function at the same time.
*Figure-Normal DHCP:
*Figure-Supported DHCP model:
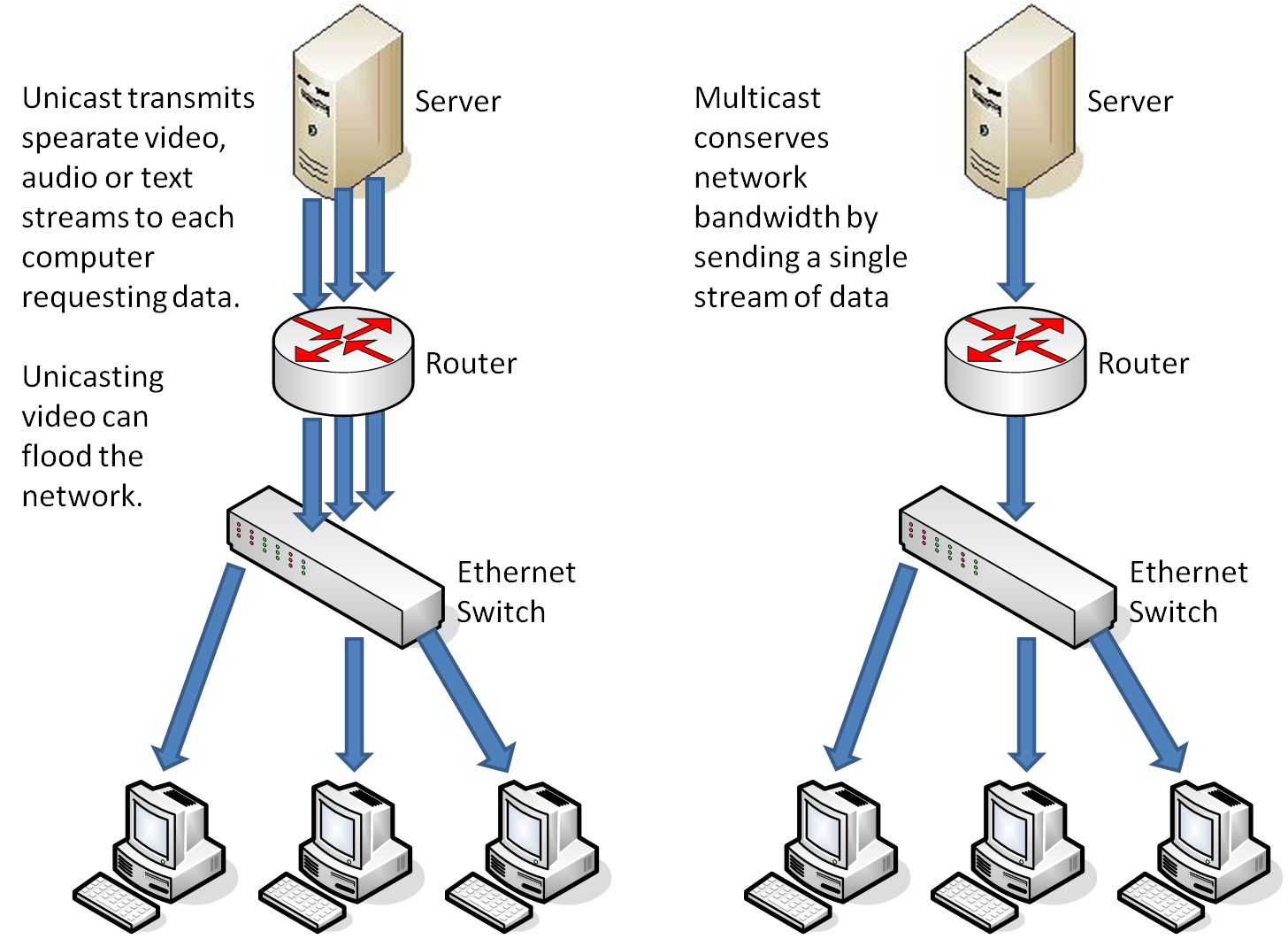
There are three ways to transfer data on the network: unicast, broadcast, and multicast. Multicast allows data to transmit to a specific list of nodes, while IGMP is able to manage the multicast groups by registering IP hosts’ dynamic group membership. With this protocol, the same data could be generated only once and then received by many users. The biggest benefit is to increase the network efficiency, especially for media transmission applications.
IGMP has 3 versions: IGMP v1, v2 and v3. IGMP v1 is defined by RFC 1112, which provides no leave and time out up to 5 minutes; IGMP v2 is defined by RFC 2236, which provides leave function to notify the query; IGMP v3 improves over IGMP v2 mainly by adding the ability to listen to multicast originating from a set of IP addresses only. Basically, IGMP v2 is the most commonly used version and can satisfy most of the applications with high network efficiency.
IGMP Snooping improves the performance of networks that carry multicast traffic. It provides the ability to prune multicast traffic so that it travels only to those end destinations that require the traffic and reduces the loading on the Ethernet network. IGMP snooping is designed to prevent hosts on a local network from receiving traffic for a multicast group they have not joined. A non-IGMP snooping switch will flood multicast traffic to all the ports.
IP multicast is growing in importance in internets today and IGMP is a key component that provides the receiver hosts and transmitting sources the capability of being dynamically added and removed on the network. All managed switches of Lantech support IGMP v1, v2, and IGMP Snooping, which are the best to be used in surveillance, transportation, automation, and entertainment applications.
The following drawings are two application examples of IGMP. You can find out that the protocol is very practical for data/ video/ voice stream transmission in a network.
IP TV figure:
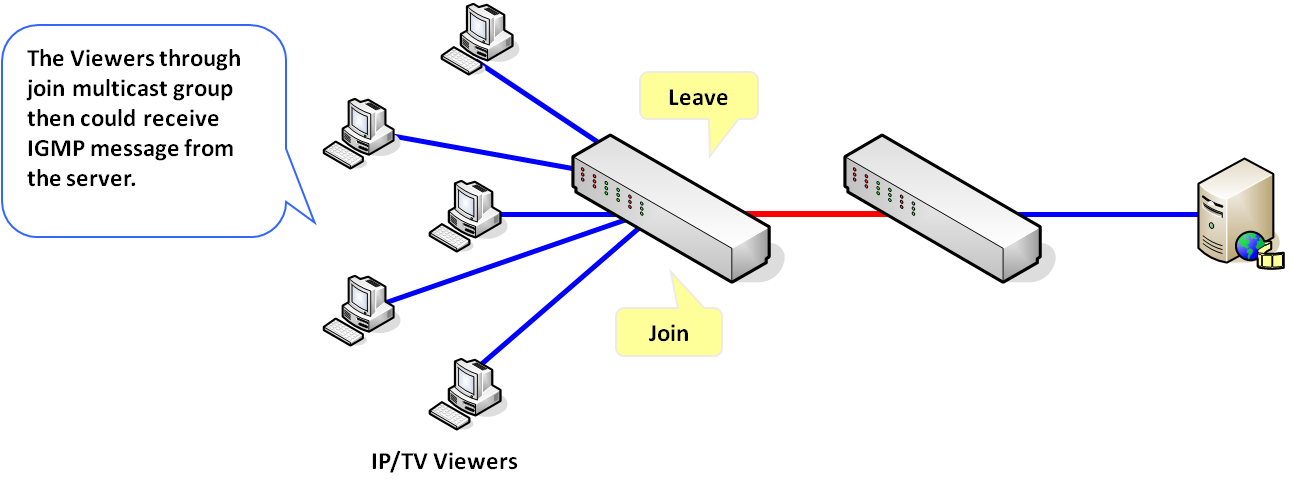
The viewers could receive IGMP message from the server by joining multicast group.
Surveillance figure:
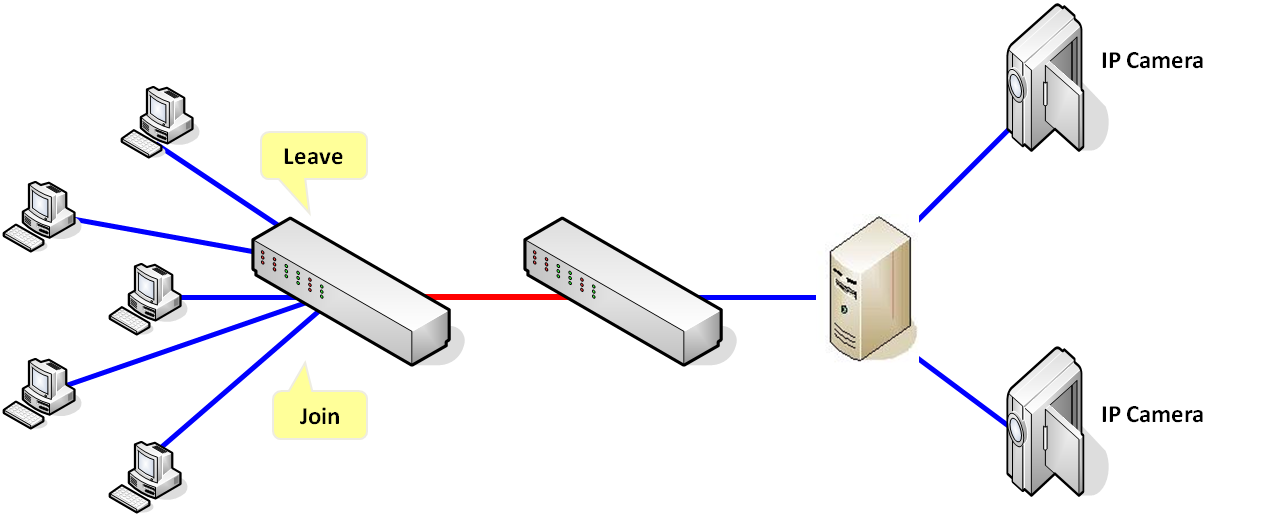
The figure shows that the IP camera captured video through the server and the switch will multicast the data to all subscribers. On the other hand, only the clients who join the multicast group could receive IGMP message from the server.
Port trunk means to combine separate ports together to create a multi-link trunk with load-balance. LACP stands for Link Aggregation Control Protocol. It is a part of an IEEE specification (802.3ad) that allows administrators to bundle several physical ports together to form a single logical channel. The advantage of it is to enlarge bandwidth with optimization.
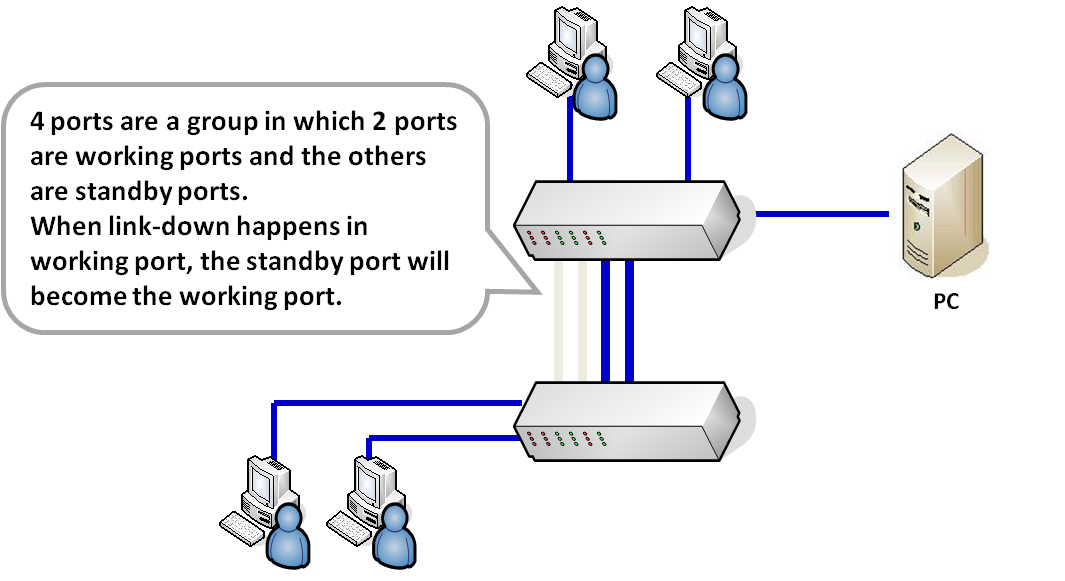
As the diagram shows, there are two switches group together with 4 ports. Two ports are working ports that will load-balance network trunk while the rest of two are standby ports, which will become working ports when working ports are link down.
To provide a better performance of Ethernet network, all of Lantech managed switches, including industrial grade and business grade, support port trunk with LACP.
For logging program messages, there’s a standard called Syslog. Syslog allows communication between the software that generates messages from the system that stores them and the software that reports and analyzes them.
Normally, Syslog provides three client modes: client only, server only, and both. When the mode is set as client only, the system event log will only be sent to the client who has logged in on the switch. When the mode is set as server only, the system log will only be sent to the Syslog server, according to the IP address in the Syslog Server IP Address column that user assigned. If the mode is set as both, the system log will be sent to client and server.
When devices are unable to communicate, Syslog also provides means to notify administrators of problems or performance. Administrators are able to receive the event log, which is set to be sent to system log server.
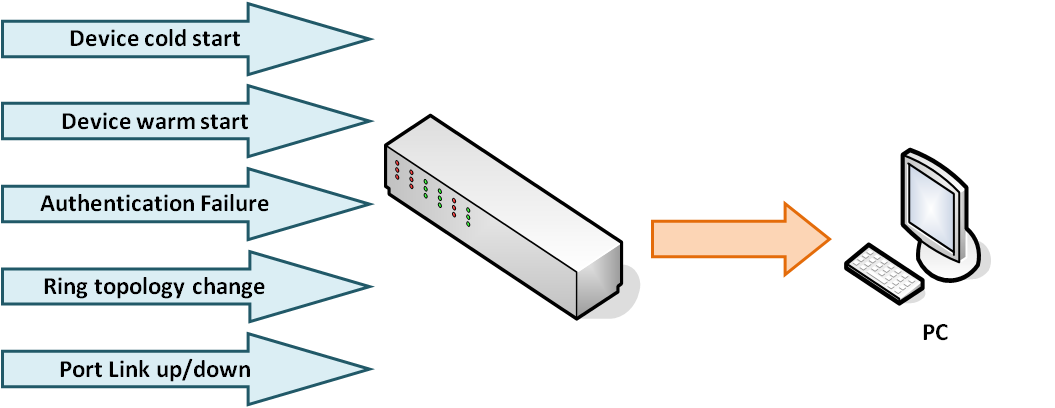
All Lantech managed switches fully support Syslog. Not only when there’s a system event such as device cold start, device warm start, authentication failure, or X-ring topology change, but also when there’s a port event such as link up, link down, or link up & link down. In conclusion, Syslog provides a basic protection for Ethernet connection.
Figure1:
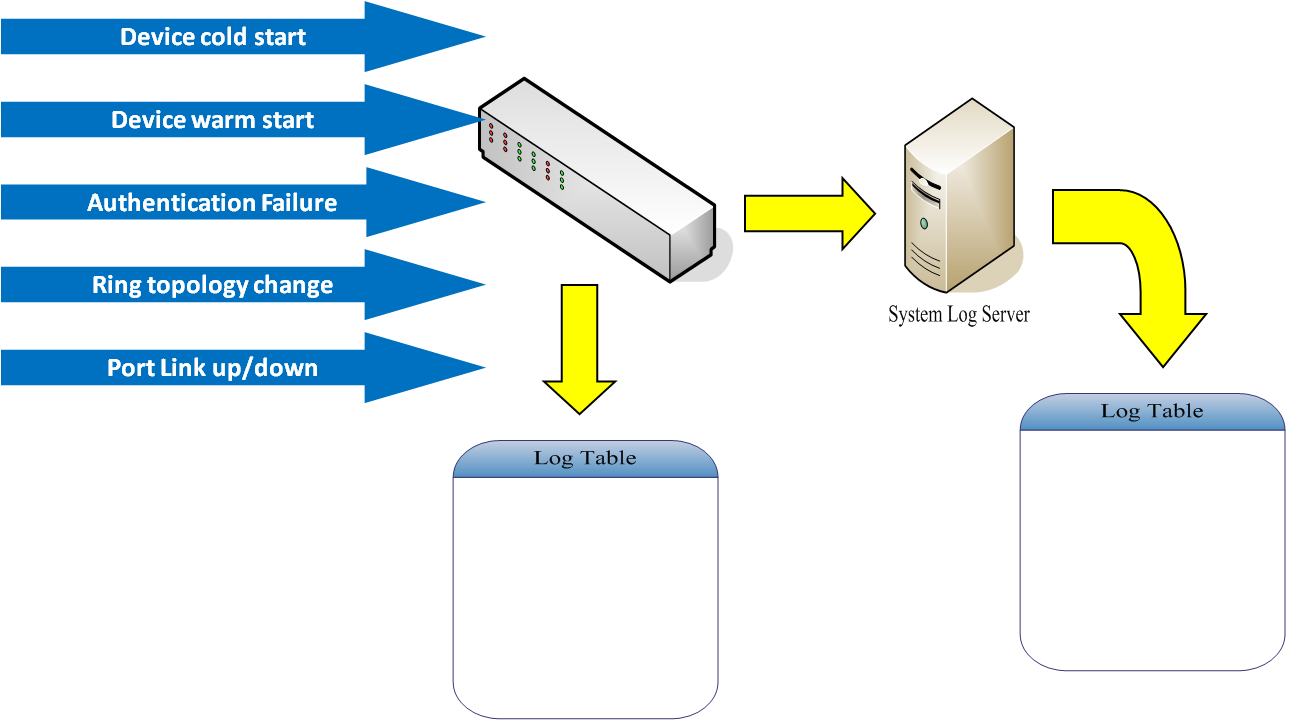
The diagram shows that when one of five events happened, it will be recorded in log table of client and system log server when Syslog mode is set as server/ client both.
A Virtual LAN (VLAN) is a logical network group that limits the broadcast domain, and allows the manager to isolate network traffic. Data communications are limited in the VLAN group, which means that only the members of the same VLAN group will receive traffic from the ones of the same VLAN group. Basically, creating a VLAN from a switch is logically equivalent of reconnecting a group of network devices to another Layer 2 switch. However, all the network devices are still plugged into the same switch physically.
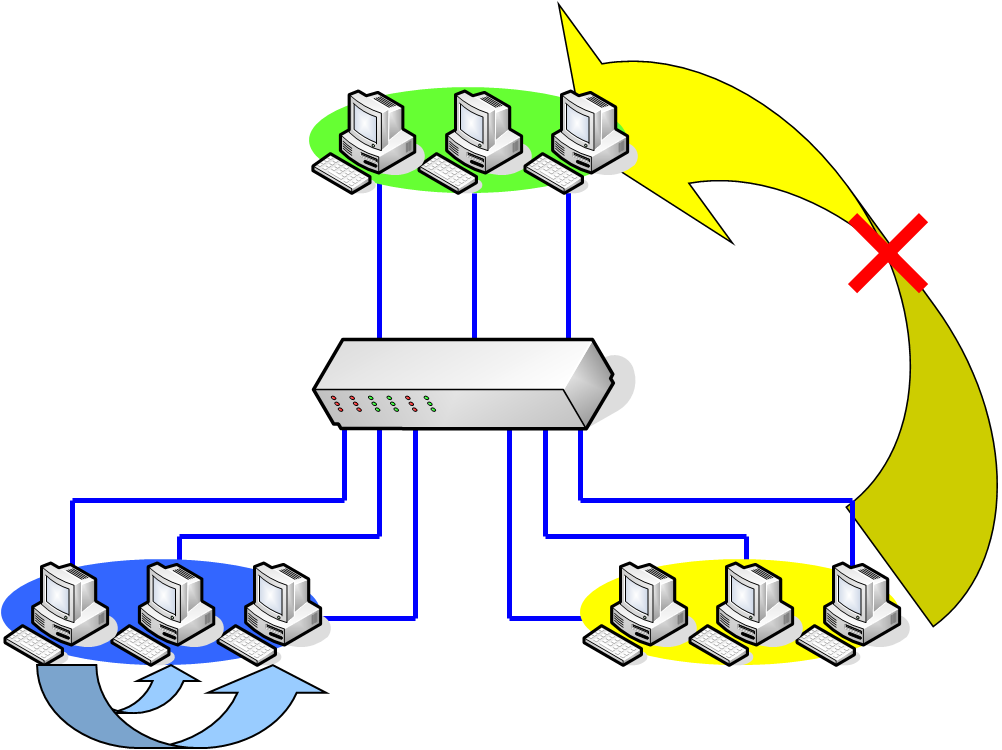
The diagram consists of three groups which connect to one switch. The members of yellow group could exchange data with each other, but couldn’t exchange data with the member of blue group or green group. This is the theorem of VLAN.
Port based VLAN
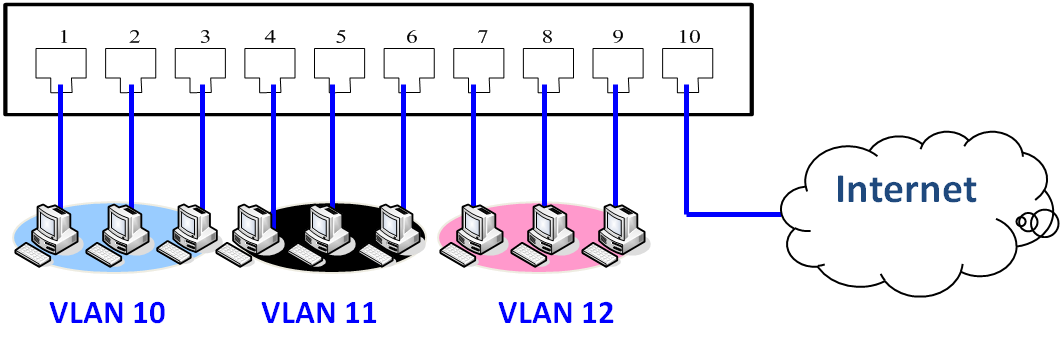
Port based VLAN allows manager to assign VLAN group based on the destination MAC address and its associated port, and the packet forwarding decision is based on the assignment. Managers are able to assign several ports among different switches as a VLAN group. Since it is based on physical layer, port based VLAN is best for small organizations.
IEEE 802.1Q Tag VLAN
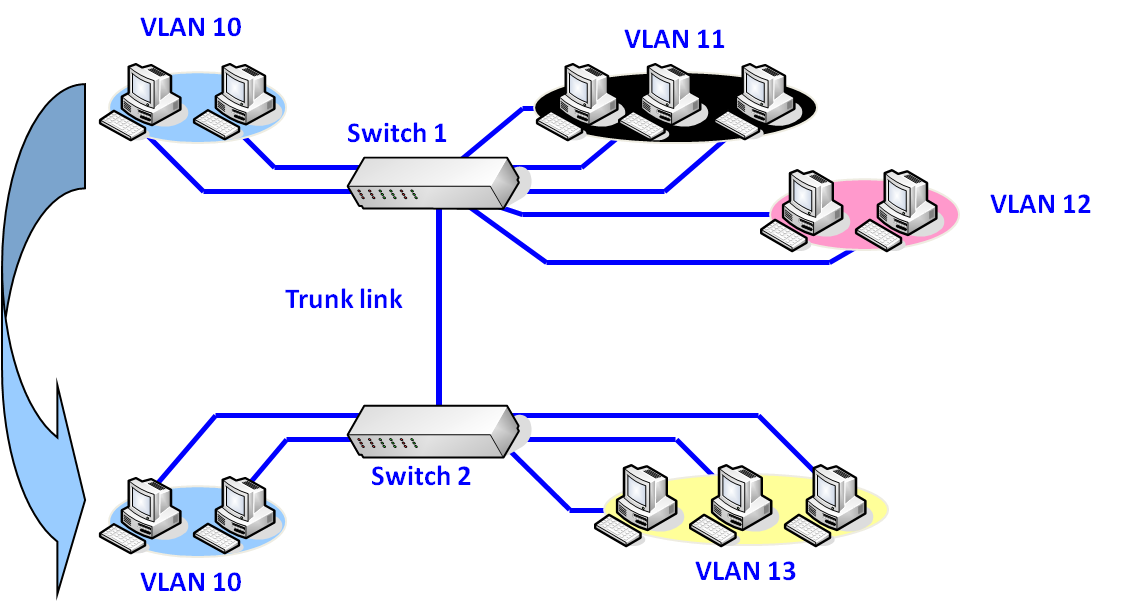
Defined in IEEE 802.1Q standard, Tag VLAN allows VLAN information to be written into the Ethernet packet itself. It adds a 32-bit field between the source MAC address and the EtherType/Length fields of the original frame which means that each packet carries a VLAN ID as it travels across the network via trunk link.
GVRP
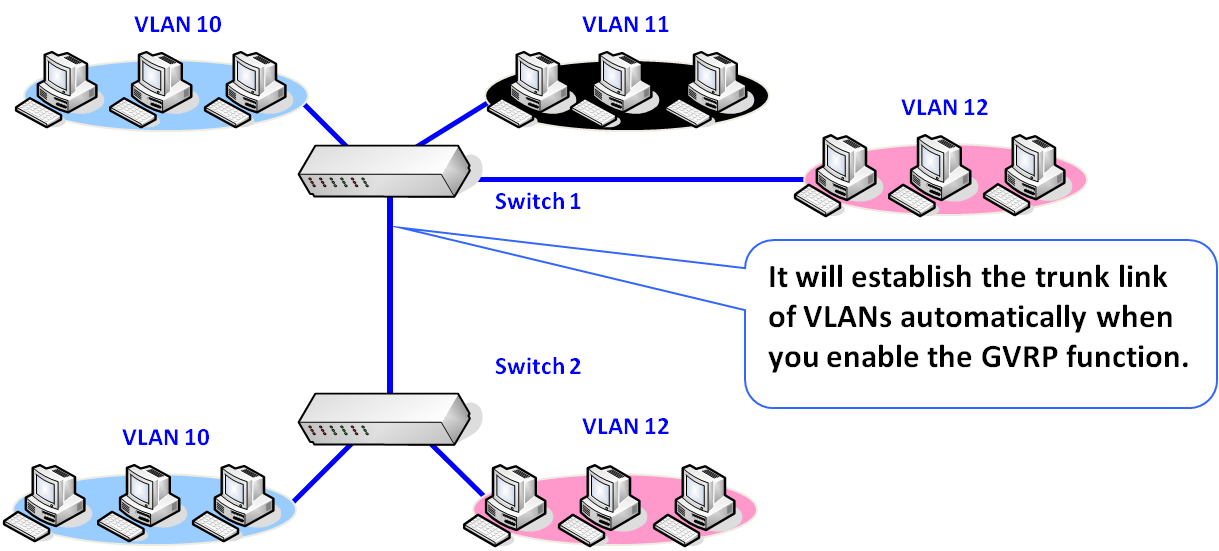
GVRP (GARP VLAN Registration Protocol) is a standard-based protocol to automatically register VLAN members on ports across the network and defines the way for different vender’s switches to exchange VLAN information.
The GVRP Bridge Protocol Data Units (GVRP BPDUs) are able to advertise static VLANs to other switches in the network. Any device that is GVRP-enabled can dynamically join the advertised VLAN by receiving the advertisements.
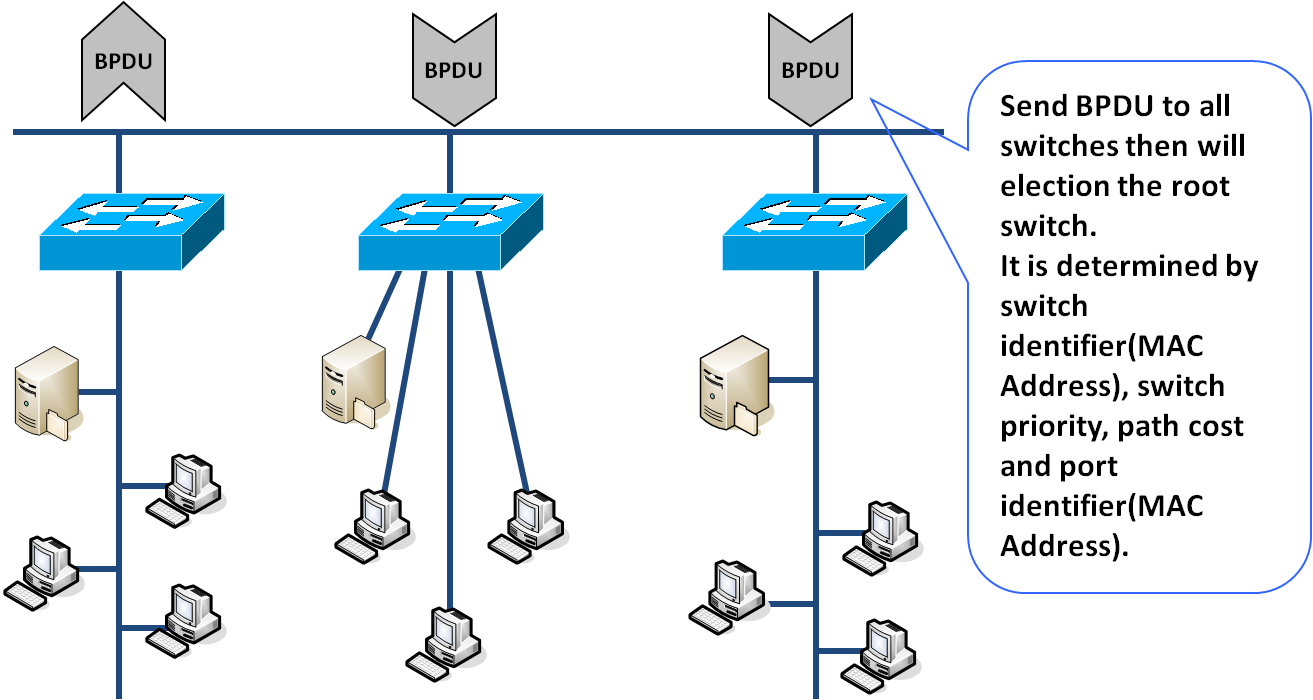
The Spanning Tree Protocol (STP) is used to provide backup links between switches, bridges or routers, and to detect and disable network loops as well. Using the STP, the switch is able to interact with other bridging devices such as an STP-compliant switch to provide backup links. When a primary link goes down, the backup links will recover the network communications automatically.
The Rapid Spanning Tree Protocol (RSTP) is an evolution of the STP. It provides faster recovery time which is about one tenth compare with the STP. Increase the reliability of network communications when there’s a topology change.
Role states:
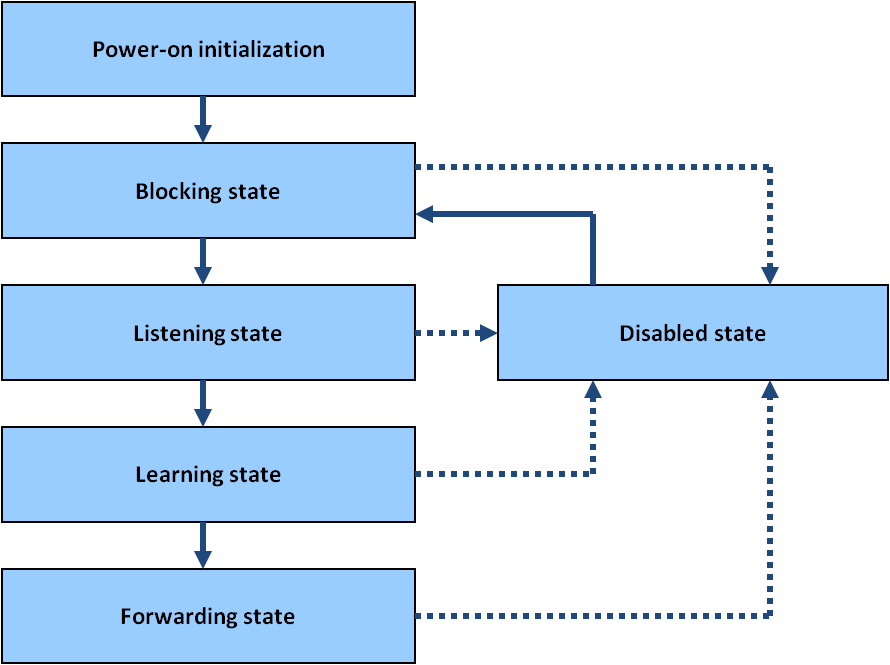
RSTP bridge port roles:
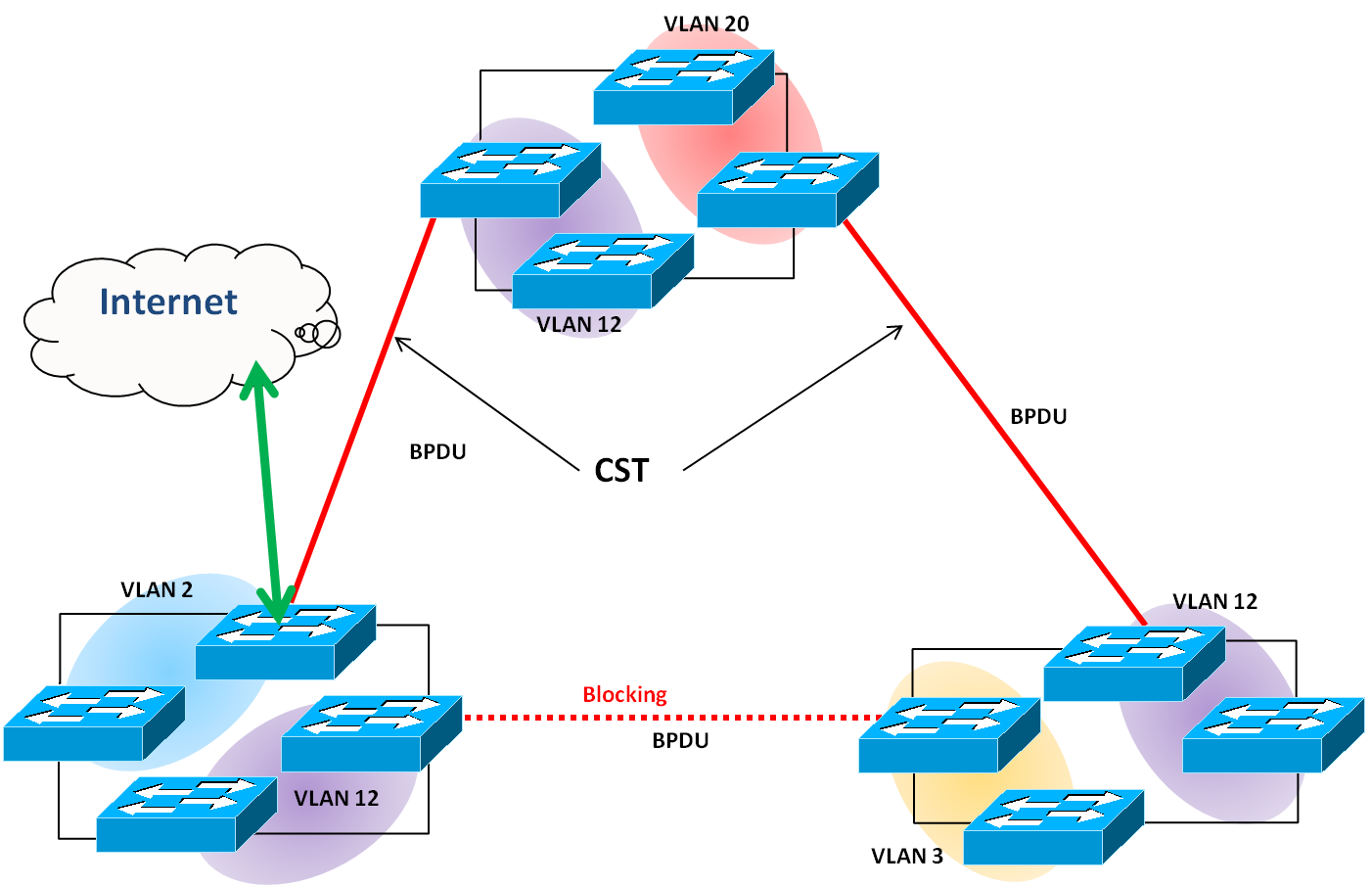
Multiple Spanning Tree Protocol (MSTP) is a standard protocol based on IEEE 802.1s. The function is that several VLANs can be mapping to a reduced number of spanning tree instances because most networks do not need more than a few logical topologies. It supports load balancing scheme and the CPU is sparer than PVST (Cisco proprietary technology).
MSTP includes all of its spanning tree information in a single Bridge Protocol Data Unit (BPDU) format. Not only does this reduce the number of BPDUs required on a LAN to communicate spanning tree information for each VLAN, but it also ensures backward compatibility with RSTP (and in effect, classic STP too). MSTP does this by encoding additional region information after the standard RSTP BPDU as well as a number of MSTI messages (from 0 to 64 instances, although in practice many bridges support less). Each of these MSTI configuration messages conveys the spanning tree information for each instance. Each instance can be assigned a number of configured VLANs and frames (packets) assigned to these VLANs operate in this spanning tree instance whenever they are inside the MST region. In order to avoid conveying their entire VLAN to spanning tree mapping in each BPDU, bridges encode an MD5 digest of their VLAN to instance table in the MSTP BPDU. This digest is then used by other MSTP bridges, along with other administratively configured values, to determine if the neighboring bridge is in the same MST region as itself.
MSTP is fully compatible with RSTP bridges, in that an MSTP BPDU can be interpreted by an RSTP bridge as an RSTP BPDU. This not only allows compatibility with RSTP bridges without configuration changes, but also causes any RSTP bridges outside of an MSTP region to see the region as a single RSTP bridge, regardless of the number of MSTP bridges inside the region itself. In order to further facilitate this view of an MST region as a single RSTP bridge, the MSTP protocol uses a variable known as remaining hops as a time to live counter instead of the message age timer used by RSTP. The message age time is only incremented once when spanning tree information enters an MST region, and therefore RSTP bridges will see a region as only one "hop" in the spanning tree. Ports at the edge of an MST region connected to either an RSTP or STP bridge or an endpoint are known as boundary ports. As in RSTP, these ports can be configured as edge ports to facilitate rapid changes to the forwarding state when connected to endpoints.
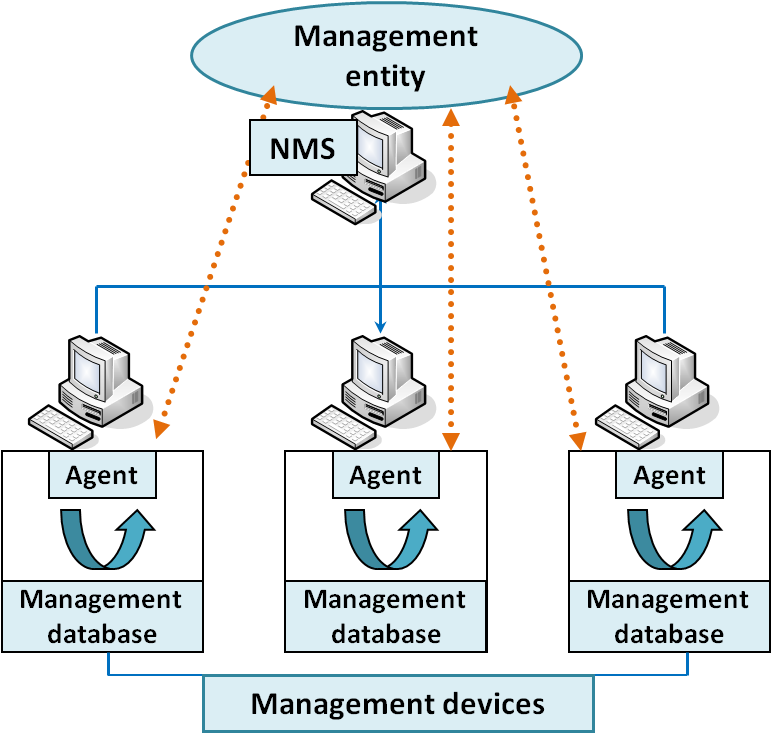
SNMP is a UDP-based network protocol and is mostly used in network management systems to monitor network-attached devices. There is a set of standards for network management, including an application layer protocol, a database schema, and a set of data objects. These standards are the basic components of SNMP.
An SNMP-managed network consists of three key components: managed devices, agents, and network-management systems (NMSs). Managed devices collect and store management information and make this information available to NMSs using SNMP. Agent has local knowledge of management information and translates that information into a form compatible with SNMP. NMS executes applications that monitor and control managed devices. NMSs provide the bulk of the processing and memory resources required for network management.
SNMP basic commands:
Triple DES. Also referred to as 3DES, a mode of the DES encryption algorithm that encrypts data three times. Three 64-bit keys are used, instead of one, for an overall key length of 192 bits (the first encryption is encrypted with second key, and the resulting cipher text is again encrypted with a third key).
Advanced Encryption Standard. A symmetric 128-bit block data encryption technique. AES works at multiple network layers simultaneously.
Address Resolution Protocol. The discovery protocol used by host computer systems to establish the correct mapping of Internet layer addresses, also known as IP addresses, to Media Access Control (MAC) layer addresses.
Dynamic Domain Name System. A method of keeping a domain name linked to a changing IP address as not all computers use static IP addresses. The Dynamic DNS service allows you to alias a dynamic IP address to a static hostname, allowing your computer to be more easily accessed from various locations on the Internet. To use the service, you must first apply an account from DDNS service provider such as www.dyndns.org.
With DDNS supported by the Load Balancer, you apply a DNS name (e.g., www.abcd.com) for your server (e.g., Web server) from a DDNS server. The outside users can always access the web server using the www.abcd.com regardless of the WAN IP of the Load Balancer.
By contacting the DNS service each time the IP address provided by the ISP changes and subsequently updating the DNS database to reflect the change in IP address. In this way, even though a domain name's IP address will change often, other users do not have to know the changed IP address in order to connect with the other computer.
Data Encryption Standard. A popular symmetric-key encryption method developed in 1975 and standardized by ANSI in 1981 as ANSI X.3.92. DES uses a 56-bit key.
Dynamic Host Configuration Protocol. A protocol that is beginning to be used quite pervasively on end-system computers to automatically obtain an IP host address, subnet mask, and local gateway information. A DHCP server dynamically supplies this information in response to end-system broadcast requests.
Demilitarized Zone. A company that wants to host its own Internet services without sacrificing unauthorized access to its private network uses it. This special function allows multiple PCs on your LAN to be exposed to the Internet without any restrictions. This is useful for some network games, net meeting, or special applications. In order to enable these functions, you have to map one LAN IP address to one WAN IP address. However, because of the security risk, you should activate these functions only if they are necessary.
File Transfer Protocol. A bulk, TCP-based, transaction-oriented file transfer protocol used in TCP/IP networks, especially the Internet.
Software (programs or data) that has been written onto read-only memory (ROM). Firmware is a combination of software and hardware. ROMs, PROMs and EPROMs that have data or programs recorded on them are firmware.
In networking, a combination of hardware and software that links two different types of networks. Gateways between e-mail systems, for example, allow users on different e-mail systems to exchange messages.
Hyper Text Transfer Protocol. A TCP-based application-layer protocol used for communicating between web servers and web clients, also known as web browsers.
Internet Control Message Protocol. A network-layer protocol that provides feedback on errors and other information specifically pertinent to IP packet handling.
The Institute of Electrical and Electronics Engineers. A professional organization that develops communications and network standards-traditionally, link-layer LAN signaling standards.
Internet Protocol. The network-layer protocol in the TCP/IP stack used in the Internet. IP is a connectionless protocol that provides extensibility for host and subnet addressing, routing, security, fragmentation and reassembly, and as far as QoS is concerned a method to differentiate packets with information carried in the IP packet header.
Internet Protocol Security. IPSec is a framework for a set of protocols for security at the network or packet processing layer of network communication.
Internet Protocol version 4. The version of the Internet protocol that is widely used today. This version number is encoded in the first 4 bits of the IP packet header and is used to verify that the sender, receiver, and routers all agree on the precise format of the packet and the semantics of the formatted fields.
The MAC (Media Access Control) address, a unique hardware address that uniquely identifies each other of a network. The MAC address is a 12 digit Hexadecimal number, in which can contain one of the following characters "0123456789ABCDEF". For example, 00-09-A3-12-34-57.
An algorithm is used to create digital signatures. MD5 is a one-way hash function, meaning that it takes a message and converts it into a fixed string of digits, also called a message digest. When using a one-way hash function, one can compare a calculated message digest against the message digest that is decrypted with a public key to verify that the message hasn't been tampered with. This comparison is called a "hashcheck."
Maximum Transmission Unit. The largest physical packet size, measured in bytes that a network can transmit. Any messages larger than the MTU are divided into smaller packets before being sent. Ethernet limits transfers to 1514(include Ethernet header) octets of data. Normally, you should leave this value as the default value. Change it only if the ISP is providing a MTU that is not optimal.
Network Address Translation. An Internet standard that enables a local-area network (LAN) to use one set of IP addresses for internal traffic and a second set of addresses for external traffic. A NAT box located where the LAN meets the Internet makes all necessary IP address translations.
NAT serves main purposes:
1) Provides a type of firewall by hiding internal IP addresses
2) Enables a company to use more internal IP addresses. Since they're used internally only, there's no possibility of conflict with IP addresses used by other companies and organizations.
It is proposed and described in RFC-1631 and is originally for solving the IP address depletion problem. Basically, "each NAT box has a table consisting of pairs of local IP addresses and globally unique addresses," by which the box can "translate" the local IP addresses to global address and vice versa.
Point-to-Point Protocol Over Ethernet. An IETF draft standard specifying how a computer interacts with a broadband modem (i.e. xDSL, cable, wireless, etc.) to achieve access to the high-speed data networks via a familiar PPP dialer such as !§Dial-Up Networking!‥ user interface. PPPoE supports a broad range of existing applications and service including authentication, accounting, secure access and configuration management. There are some service providers running of PPPoE today.
Point-to-Point Tunneling Protocol. It is a protocol that allows corporations to extend their own corporate network through private !§tunnels!‥ over the public Internet effectively.
A packet is the unit of data that is routed between an origin and a destination on the Internet or any other packet-switch network. When any file (e-mail message, HTML file, Graphics file, and so forth) is sent from one place to another on the Internet, the TCP/IP divides the file into "chunks" of an efficient size for routing. Each of these packets is separately numbered and includes the Internet address of the destination. The individual packets for a given file may travel different routes through the Internet. When they have all arrived, they are reassembled into the original file (by the TCP layer at the receiving end).
The ability to log onto a network from a distant location. Generally, this implies a computer, a modem, and some remote access software to connect to the network.
Routing is usually performed by a dedicated device called a router. Routing is a key feature of the Internet because it enables messages to pass from one computer to another and eventually reach the target machine. Each intermediary computer performs routing by passing along the message to the next computer. Part of this process involves analyzing a routing table to determine the best path.
Simple Network Management Protocol. SNMP is the protocol governing network management and the monitoring of network device and their functions. It is not limited to TCP/IP network.
A session is a series of interactions between two communication end points that occur during the span of a single connection. Typically, one end point requests a connection with another specified end point and if that end point replies agreeing to the connection, the end points take turns exchanging commands and data. The session begins when the connection is established at both ends and terminates when the connection is ended.
A syn-flood is a stream of packets that each initiate a new TCP session, but no follow-up packets are sent to complete the connection handshake. Target at a service port, this will usually overload the server such that it cannot respond to any real connection requests from real clients, as the server can only keep a limited number of connection slots active at any one time. A syn-flood is a class of attack known as a denial of service attack. The origin for syn-flood packets can be set to any address on the net, making location of the source of a syn-flood attack, difficult.
This feature can send real time system information on the web page or to the specified PC. If you want to receive real time system information to specified PC, you need to install syslog software. www.winsyslog.com offer trial version software.
Type of Service. A bit field in the IP packet header designed to contain values indicating how each packet should be handled in the network. This particular field has never been used much, though.
A method of bridging used in Ethernet and IEEE 802.3 networks by which frames are forwarder along one hop at a time, based on forwarding information at each hop. Transparent bridging gets its name from the fact that the bridges themselves are transparent to the end-systems.
Virtual Private Network. VPN provides a means for remote computers to securely communicating with each other across a public wide area network (WAN), such as the Internet. A VPN connection may be used to link two local area networks (LANs) or for a remote dialup user to connect to a private LAN.
A Virtual Server is defined as a service port, and all requests to this port will be redirected to the computer specified by the server IP. For example, if you have an FTP Server at 205.20.45.34 and a Web server at 205.20.45.35 in your LAN, then you need to specify the following virtual server mapping table.
2020 © Lantech Communications Global, Inc. ALL Rights Reserved. Privacy Policy | Terms of Service






